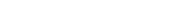Some examples include the case of the Stuxnet worm discovered in June 2010 when it infected Siemens industrial control systems. Arguably created to sabotage the Iranian nuclear plan, this virus was characterised by capabilities that could stop production and manufacturing systems or alter the features of final products posing a danger to the health of the final consumers. Another computer worm, the Duqu, was developed with the aim to gather and steal information from the infected machines. In 2004, British Telecom experienced a minor short circuit. This had several effects: 130,000 users’ telephone, fax and internet systems lost their connectivity; 31 bank branches closed down; automated teller machines collapsed; and emergency hotlines were inaccessible. The estimated damage was more than US$ 7 million per day. This specific example illustrates the huge impact that a seemingly small failure could have on the entire system of interconnected entities. The risks from cyberspace have been identified by the US and UK governments as a high priority risk and “one of the most serious economic and national security threats our nation faces”.
Cyber security the protection of valuable intellectual property and business information in digital form against theft and misuse is an increasingly important issue in today’s networked world. It impacts all industries from healthcare to finance and generally anybody who uses the internet is at risk of becoming a cyber-victim and vulnerable to attack by sophisticated cyber criminals. Given the increasing pace and complexity of the threats companies must adopt, approaches to cyber security that will require more engagement from CEO and other senior managers to protect critical business information. Given the level of information shared in global supply networks, the supply chain is one of the most critical areas of the business where cyber risks should be identified and managed.
Information-based collaborative supply chains have emerged in most industries such as apparel, automotive and retail to name a few and concepts like adaptability, responsiveness, agility and lean are a key focus in modern supply chains. These concepts depend on real-time information availability to all supply chain partners, which makes the impacts of information failure more widespread. Given these trends, supply chain management is increasingly dependent on information systems, particularly the internet having a significant role in business transactions. The adoption of information systems to share data with buyers and suppliers has resulted in the growth of virtual supply chains where the key driver in a virtual supply chain would be information rather than actual physical flow of paper. The benefits in replacing inefficient and costly paper based processes with virtual equivalents can be seen in the growth of inter-organisational schemes such as EDI. At the same time, the vulnerability of these systems to attack from cyber enemies is growing.
The growth of information systems and the universal access to computers have enabled hackers and terrorists to attack information systems crippling global supply chains. Opportunities for attack include malware inserted into software or hardware and vulnerabilities found by hackers prodding software which can be internal. In recent years Apple, Hewlett-Packard and Sony have shipped pre-owned laptops, hard drives and other devices with viruses, worms and Trojans on them. Today organisations have a better understanding about these types of information risks and they are more cautious in their approach towards managing risks better. However, these efforts concentrate on information risks along organisational boundaries and are fragmented in their approach, while the increased pressure to work on real time information facilitated by intranet and extranet, demand new initiatives to manage these risks. A director for the Centre of Strategic and International Studies technology and public policy programme states “organisations need to realise that their borders are porous…it’s not just how secure you are, but how secure the people you connect with are”.
These threats represent a risk for information confidentiality, privacy, integrity and require new approaches for risk management. Notwithstanding the significant interest in managing risks in complex global supply chains, less attention has been applied to managing cyber risks. Even less is known about how organisations have integrated information and cyber risk into supply chain risk management.
Cyber and information threats require new approaches in the field of supply chain risk management. It is not surprising therefore that The World Economic Forum suggests that cyber and information risks should be included in the wider organisational approaches for improving supply chain resilience.
In this article we share the responses of senior executives and managers from six medium to large international companies operating globally regarding the rising threat of cyber risks in supply chains.
How do companies perceive the threat of cyber security and how do they evaluate and incorporate the related risk within the company’s wider supply chain risk strategy?
Whilst supply chains are becoming more reliant on information and communication technologies, the challenge is to create cyber resilient supply chains. The respondents generally agreed that the trends of the past decades have contributed to risk and complexity in supply chains experienced today: From the introduction of Just-in-Time philosophy in the 80’s, the competitive scenario has evolved through outsourcing and IT solutions and it is now characterized by risk and uncertainty. In particular, as shown in Table 1, the most perceived cyber and information risks depend on the industry sector in which the company operates. When examining risks, companies of the finance sector are highly concerned with franchise risks, while for the insurance companies the potential loss of data is of paramount importance to maintain a good reputation and be able to compete in the marketplace. According to the manufacturing companies, focusing on production processes, the main risks are related to the achievement of regulatory requirements that could, in turn, result in the closure of business. Finally, companies operating in the logistics industry stated that the potential leakage of customer information is critical: In a competitive environment where logistics companies have realised the need for enhancing closer relationships with customers and for nurturing collaboration among business partners, the loss of data could negatively affect trust on which these relationships are based.
Given this scenario, all companies interviewed recognize the importance of an integrated approach to cyber supply chain risk management, both within the companies’ boundaries and beyond them. A supply chain director of a procurement outsourcing and consulting company affirmed that all the functions of a company are central to risk management in the supply chain. Discussions also highlighted the requirements from supply chain and information system managers to collaborate with the aim of understanding various cyber and information risks mitigation variables but also the mutual relationships among them. Notwithstanding this, the majority of interviewed companies (52%) demonstrate a lack of alignment between supply chain risk management and information systems (Figure 1).
Risks to information are assessed using a variety of approaches, often based around business impact assessment; but there is no standard approach, nor agreement on the measurement of impact. This approach limits the understanding of information risk in the supply chain and may mean that cyber risks are not incorporated within the company’s wider supply chain risk strategy.
How are companies protecting their supply chain in order to prevent cyber security breaches?
Given the increasingly reliance on suppliers to enhance the efficiency of business processes, companies are highly concerned about external supplier security arrangements. However, the results indicate that the majority (approximately 85%) of the interviewed companies typically do not take a supply chain view of cyber and information risk and rather focus on individual relationships with Tier 1 suppliers. This approach means that risks such as the sharing of information between tiers are not evaluated.
Typical approaches to manage the information security of Tier 1 suppliers involve a customer requiring a supplier to either meet individual contractual arrangements or individual organisational policies. From the supplier perspective, such approaches are inefficient, as each individual customer will have different requirements. It is noteworthy that the use of (or reference to) known global information security standard (such as the ISF Standard of Good Practice, ISO/IEC 27001 and ISO/IEC 27002 or ISACA CObIT) is the lowest of the categories examined, as shown in Figure 2.
Figure 2 illustrates, from an information perspective, there is little agreement on the standards and processes that should be used to protect information transmitted or shared across the supply chain. Additionally, most information security standards are written to apply to one organisation, and consequently are not applied across the extended supply chain. As a result, the majority of efforts are focused on protecting the confidentiality, integrity and availability of information through its lifecycle – creation, transmission, processing, storage and destruction. This involves deploying and implementing information security controls such as encryption, identity and access management and incident management.
Cyber and information risk management remains a complex management process, due to the dependency on a number of interconnected variables. Respondents agreed on the significance of understanding exposures (industry-, and supplier- specific) as well as internal and external risk factors.
| Sector | Risks | Impacts |
| Finance | – Franchise Risks – CIA – Fines – Regulatory Risks |
Vary depending on issue and data. We look at type, volume, frequency, whether it gets moved.. |
| Insurance | – Loss of data – Fines – Suppliers Financial Ratings – Integrity of data |
Reputational damage is the biggest impact. If we lose our data we won’t be seen as the best in the industry! |
| Production | – Integrity – Security – Regulatory Requirements (across borders and industries) |
Impacts vary widely. We try to focus on enterprise impacts, i.e. Regulatory (PCI, Privacy). For example, with food traceability if you couldn’t comply, the worst case scenario is losing your business. |
| Logistics | – Customer Information Leakage | – Brand reputation – Fines from data protection commissioner – Loss of customers |
How are companies strengthening their supply chains in order to make them more resilient to cyber attacks?
Our analysis indicates that companies are starting to collaborate across supply chains aligning their processes, seeking greater flexibility and visibility in their supply chains. Flexibility, risk governance, alignment, integration, information sharing, data, models and analytics, and rationalization have been identified as the most effective enablers of supply chain risk reduction. Less focus has been applied to incorporating cyber risk into the overall supply chain risk strategy to date. Therefore, our results on resilience, suggests that though companies have made some progress in supply chain resilience, many have not secured their supply chains from cyber and information risks. However, a few companies in our sample exhibited the following trends:
- Greater attention paid to business continuity by suppliers and customers, with customers asking suppliers to demonstrate their business continuity procedures.
- Greater use of baseline information security arrangements and associated tools to assess suppliers’ compliance and performance.
- Greater use of supplier assessment both pre-contract and during the contract lifecycle.
- Increasing levels of involvement of information risk professionals in supply chain risk management.
Cyber and information risks in the supply chain can have a huge impact on the business, and given the complexity of this area it is not surprising that companies are only beginning to realise the real threat from cyber space. These threats can be critical and it is vital that companies involve information risk professionals into the broader supply chain risk management strategy to strengthen the resilience of their supply chains.
Steps towards cyber-resilience
The research findings above indicate that most of the companies do not take a supply chain view of information risk. This is largely due to the lack of collaboration between information systems and supply chain professionals. Furthermore companies evaluate information risks with each tier one supplier rather than focusing on the impacts of these risks across the nodes and links that the tier one supplier could be connected too and hence, spreading the risk. Such an approach limits the understanding of information risk in a supply chain and may mean that risks such as the sharing of information between tiers is not evaluated.
In addition from an information perspective, there is little agreement on the standards and processes that should be used to protect information used, transmitted or shared across the supply chain in most if not all industry verticals. Additionally, most information security standards are written to apply to one organisation, and consequently do not examine or work well at the level of the supply chain.
The journey to cyber resilience in supply chains should start with the following steps, companies and must:
- Appoint a cyber risk champion – this individual leads and oversees the process of aligning information systems and supply chain managers, develops the key competencies required to create a cyber resilient culture and manages the engagement of all individuals that are required to proactively deploy the appropriate defenses against cyber threats. In addition the cyber risk champion is responsible for the implementation of the following five steps.
- Actively engage senior leaders to co-ordinate the cultural change required to incorporate cyber risks into the broader supply chain risk portfolio and support the progress towards cyber resiliency.
- Develop a register of cyber risks based on a prioritised list of information assets, needing protection.
- Assemble cyber-security teams that consist of key individuals across the organisation from marketing, supply chain and information systems to uncover cyber threats and deploy proactive defences.
- Identify ‘what if’ scenarios and develop capabilities to aggregate relevant information to proactively manage cyber risks.
- Run cyber war games to test for weaknesses and improve the organizations ability to respond effectively to cyber risks and in real time.
Conclusions
Few companies have yet formalised a supply chain risk management strategy, even less are aware of how to respond to the growing threats of cyber-attacks. Therefore, companies are required to build new levels of collaboration among security, information systems and supply chain managers. This article describes the challenges companies are facing with the rising threat of cyber risks and highlights the steps they must take towards cyber resilience. This will be a useful start for supply chain managers as they plan to better secure their supply chains against cyber-attacks.
In the future, the vulnerability of supply chains to cyber-attacks will increase as supply chains are becoming more virtual in their management and therefore exposed to such attacks. CEO’s must recognize these threats and focus on securing their supply chains, so that they are less exposed, whilst at the same time, they must ensure that the effective sharing of information across supply networks is not compromised.
Figure 1: Alignment between supply chain risk management and information systems.
Figure 2: How information security arrangements are agreed with external suppliers (% agreeing).
Cyber security facts
Estimate of threat (U.S.): 1.8 billion cyber-attacks each month.
Record of cyber-attacks: Less than 1% reported due to lack of knowledge and liability concerns.
Spread of cyber risk threat: Unknown.
Protection against cyber-attacks: Only about 30% of companies encrypt data.
Estimated global cost of cybercrime: 400bn USD annually.
Terje Stolte
Terje Stolte, PhD, is a Management Consultant for Valcon A/S. His PhD is in the area of supply chain risk management from the University of Hull (UK). Terje has a number of years of industry experience ranging from working in training and development, business optimization, as well as a research associate for a UK university.
Omera Khan
Omera Khan PhD, is Professor of Operations Management at the Technical University of Denmark. Omera has gained international recognition for her research in supply chain risk management. She has published her research in leading journals and has contributed to several book chapters and is lead-author of the “Handbook for Supply Chain Risk Management: Case Studies, Effective Practices and Emerging Trends”. Omera is a highly acclaimed presenter and is regularly invited as a keynote speaker at global conferences and corporate events.